We’re excited to introduce Amazon Bedrock AgentCore Identification, a complete identification and entry administration service purpose-built for AI brokers. With AgentCore Identification AI, agent builders and directors can securely entry AWS sources and third-party instruments corresponding to GitHub, Salesforce, or Slack. AgentCore Identification gives sturdy identification and entry administration at scale in order that brokers can entry your sources or instruments both on behalf of customers or themselves with pre-authorized person consent to reduce the necessity for customized entry controls and identification infrastructure improvement.
As organizations deploy AI brokers into manufacturing environments, they face a essential problem: methods to securely handle identification and entry at scale. Purposes have to authenticate customers for invoking AI brokers, and these brokers have to entry a number of instruments and providers, keep audit trails, and combine with present enterprise identification programs—all whereas avoiding information leakage and sustaining compliance with organizational necessities. These necessities develop into exponentially extra complicated when brokers function throughout disparate programs, act on behalf of various customers, and have to entry sources and instruments in each AWS and exterior third-party providers.
On this submit, we look at how AgentCore Identification solves these agentic AI safety challenges. We begin by exploring the core identification and safety wants for enterprise AI brokers, then dive into the structure of AgentCore Identification for managing agent identities and credentials. We then reveal methods to implement safe agent authentication by way of a sensible buyer help use case and conclude with greatest practices for enterprise-grade safety at scale.
Agentic AI safety at scale
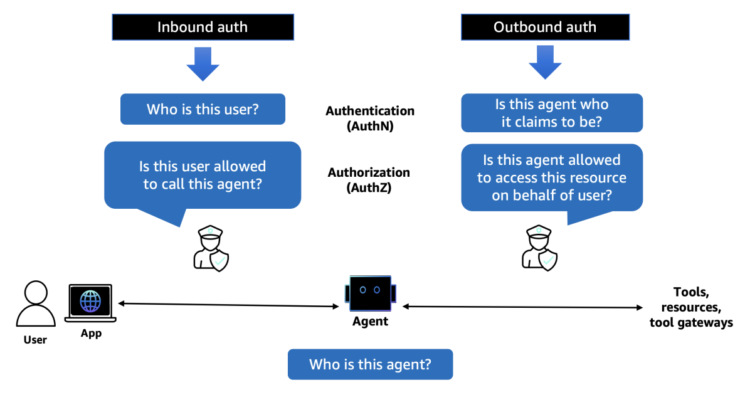
Constructing safe AI brokers for enterprise deployment presents distinctive identification and entry administration challenges that conventional utility safety fashions weren’t designed to deal with. The next diagram illustrates the areas the place entry management by way of authentication and authorization is required in a typical agentic workflow.

Let’s look at the particular safety necessities that make agentic AI programs notably complicated:
Inbound authentication: Who can entry the agent?
When customers or purposes invoke an AI agent, you should confirm their identification and decide what they’re licensed to do. This inbound authentication should help a number of patterns:
- Consumer authentication: Verifying human customers accessing brokers by way of net purposes or APIs
- Service authentication: Validating different providers or brokers that want to speak together with your agent
- Multi-tenant isolation: Blocking customers from completely different organizations from accessing one another’s information
Outbound authentication: What can the agent entry?
AI brokers have to work together with varied sources and instruments to perform duties. This outbound authentication presents its personal challenges:
- Performing on behalf of customers: Brokers usually have to entry user-specific sources (corresponding to their Google Drive or Slack workspace) with acceptable permissions
- Service-to-service authentication: Brokers may want their very own credentials to entry shared sources or APIs
- Token administration: Securely storing and managing OAuth entry tokens, API keys, and different credentials with out exposing them to potential threats
Enterprise integration necessities
Trendy enterprises have invested closely in identification infrastructure, and AI brokers should combine seamlessly:
- Identification supplier compatibility: Supporting present programs corresponding to Amazon Cognito, Okta, or Microsoft Entra ID (previously Azure Lively Listing).
- Customary protocols: Utilizing OAuth 2.0, OpenID Join, and different trade requirements
- Strong entry controls: Implementing least-privilege entry and steady verification
Compliance and auditability
For monetary providers firms and different regulated industries, each agent motion have to be traceable:
- Complete audit trails: Logging who accessed what, when, and on whose behalf
- Knowledge isolation: Avoiding cross-contamination between completely different customers’ information
- Regulatory compliance: Assembly necessities for information safety and privateness laws
And not using a purpose-built answer, builders spend months constructing customized authentication programs, implementing token vaults, managing OAuth flows, and creating audit mechanisms—all whereas attempting to keep up safety greatest practices.
AgentCore Identification: Foremost options
AgentCore Identification addresses most of those challenges by offering a centralized functionality for managing agent identities, securing credentials, and supporting seamless integration with AWS and third-party providers by way of Sigv4, standardized OAuth 2.0 flows, and API keys.
The primary parts supplied with AgentCore Identification embrace:
- Agent identification listing: Create, handle, and set up agent and workload identities by way of a unified listing service that acts as the only supply of fact for the agent identities inside your group.
- Agent authorizer: Validates whether or not a person or service is allowed to invoke an agent or not.
- Useful resource credential supplier: Shops the configuration for an agent that should get credentials to entry downstream useful resource servers. It subsequently retrieves credentials of downstream useful resource servers corresponding to Google or GitHub to entry them, for actions like in instance fetching emails from Gmail or including a gathering to Google Calendar.
- Useful resource token vault: Shops person’s OAuth entry tokens and permits brokers to retrieve them securely to carry out actions on behalf of customers and scale back pointless person consents.
AgentCore Identification implements authentication and authorization controls that confirm every request independently, requiring specific verification for entry makes an attempt no matter supply. It integrates seamlessly with AWS providers whereas additionally enabling brokers to securely entry exterior instruments and providers. You should use AgentCore Identification for securing entry to the brokers, and for securing entry to the sources or instruments that your brokers entry on behalf of customers, as proven within the following diagram.

Whether or not you’re constructing easy automation scripts or complicated multi-agent programs, AgentCore Identification gives the identification basis to assist your purposes function securely and effectively.
Distinct agent identities
Every agent receives a novel identification with related metadata (corresponding to identify, Amazon Useful resource Title (ARN), OAuth return URLs, created time, final up to date time) that may be managed centrally throughout your group. This workload identification strategy means brokers are first-class residents in your safety structure, not simply purposes masquerading as customers.
Twin authentication mannequin
AgentCore Identification implements a twin authentication strategy:
- Inbound authentication: Validates customers and purposes trying to invoke brokers
- Helps AWS Identification and Entry Administration (IAM) credentials (SigV4) for AWS authentication
- Integrates with OAuth 2.0 or OpenID Join identification suppliers
- Supplies JSON Net Token (JWT) token validation
- Outbound authentication: Permits brokers to securely entry sources:
- The token vault gives safety for storing OAuth 2.0 entry tokens, OAuth consumer credentials, and API keys with complete encryption at relaxation and in transit.
- Helps each two-legged OAuth (machine-to-machine) and three-legged OAuth (on behalf of customers)
- Pre-configured integrations with authorization suppliers for common providers corresponding to GitHub, Slack, or Salesforce.
Safe token vault
The safe token vault is a key factor of the safety mannequin for AgentCore Identification:
- Encryption: Credentials are encrypted utilizing buyer managed AWS Key Administration Service (AWS KMS) keys
- Entry management: Credentials certain to particular agent-user mixtures
- Zero token sharing: Avoids credentials from being accessed throughout customers or brokers
Seamless SDK integration
Seamless integration with the AgentCore SDK by way of declarative annotations corresponding to @requires_access_token and @requires_api_key that routinely deal with credential retrieval and injection, decreasing boilerplate code and potential safety vulnerabilities.
The best way to get began
Let’s stroll by way of a sensible instance of deploying a developer productiveness agent that helps engineering groups handle their GitHub repositories, monitor points, and streamline their improvement workflow, as proven within the following diagram.

This agent will authenticate builders utilizing OAuth after which entry GitHub to assist them handle repositories, monitor points, and overview pull requests on their behalf. You’ll be able to observe the entire instance in this pocket book.
Stipulations
Step 1: Arrange your identification supplier
First, configure your identification supplier for agent customers. You should use an OAuth 2.0-compatible identification supplier of your selection. For this instance, we use Amazon Cognito with a helpful script offered in the pocket book. We are able to then map the attributes required both immediately or by counting on AWS Secrets and techniques Supervisor for storing and retrieving this data securely.
Step 2: Create your agent with JWT authentication
Configure your agent runtime to just accept JWT tokens out of your identification supplier:
Step 3: Configure OAuth credential supplier for GitHub
Arrange the OAuth supplier to allow your agent to entry GitHub providers. AgentCore Identification gives preconfigured settings for common providers:
Step 4: Implement the agent with automated token dealing with
Create instruments with AgentCore SDK annotations to routinely deal with the three-legged OAuth course of. The @requires_access_token decorator manages the complete OAuth stream, together with person consent. You’ll be able to verify the total code for this instance in the pocket book, however we spotlight the important thing components within the snippet beneath:
Step 5: Deploy and take a look at
Deploy your agent utilizing the AgentCore CLI:
When customers invoke your agent with their JWT token, AgentCore Identification will:
- Validate the incoming JWT token
- Set up the person’s identification
- Set up its personal identification and acquire a workload entry token for the person and agent pair
- When the agent wants GitHub entry, use the workload entry token to routinely deal with the person consent as a part of the three-legged OAuth stream by offering an authorization URL
- Securely retailer and retrieve tokens from the vault
- Inject tokens into your perform calls
Let’s discover an indication of how an utility would appear to be for this instance.
As you possibly can see, the agent seamlessly authenticates customers and accesses their GitHub repositories with out exposing credentials or requiring guide token administration. The whole OAuth stream, together with person consent and safe token storage, is dealt with routinely by AgentCore Identification.
Clear up
When you’ve accomplished the instance offered, you possibly can clear up the sources with the instructions beneath to keep away from pointless costs in your account. Keep in mind to exchange the supplier ID with your individual ID.
Integration with AgentCore atmosphere and identification suppliers
AgentCore Identification is designed to work seamlessly with the broader AgentCore atmosphere and your present identification infrastructure.
AgentCore service integration
- AgentCore Runtime: Runtime, powered by AgentCore Identification, assigns distinct identities to AI brokers and seamlessly integrates together with your company identification supplier corresponding to Okta, Microsoft Entra ID, or Amazon Cognito, amongst others.
- AgentCore Gateway: When utilizing Gateway to show instruments utilizing Mannequin Context Protocol (MCP), AgentCore Identification handles authentication for each incoming agent requests and outgoing device calls
Identification supplier compatibility
AgentCore Identification helps OAuth 2.0 or OpenID Join-compatible identification suppliers, and suppliers accessible by way of API keys. For instance, Amazon Cognito, Okta, and Microsoft Entra ID, amongst others.
Clients who use AgentCore Identification by way of both AgentCore Runtime or AgentCore Gateway, don’t incur any further costs for his or her use of AgentCore Identification. For different eventualities, you pay for under what you utilize and are charged based mostly on the variety of requests from the agent to AgentCore Identification for an OAuth token or an API key. For extra data on pricing, check with the AgentCore public pricing.
Safety concerns and greatest practices
When implementing AgentCore Identification, observe these safety greatest practices:
Precept of least privilege
Decrease safety dangers by limiting agent entry to solely important sources and capabilities:
- Grant brokers solely the minimal permissions wanted
- Usually audit and overview agent permissions
Agent and person identities based mostly entry
Set up clear identification verification and administration protocols for each human customers and AI brokers:
- Present person identification in a verifiable type
- Handle agent identities
Token administration
Defend authentication credentials by way of correct token lifecycle administration:
- Allow automated token refresh to reduce credential publicity
- Use
force_authentication=Truefor delicate operations - Implement token expiration insurance policies acceptable on your use case
Audit and monitoring
Preserve visibility into agent actions to detect anomalies and guarantee compliance with organizational necessities:
- Allow Amazon CloudWatch logging for the agent operations
- Arrange alerts for uncommon authentication patterns
- Usually overview audit logs for compliance
Multi-tenant safety
For software program as a service (SaaS) suppliers and multi-tenant environments:
- Configure separate credential suppliers per tenant
- Use tenant-specific JWT claims for validation
- Implement further authorization checks in your agent logic
Conclusion and future outlook
Amazon Bedrock AgentCore Identification transforms how organizations safe AI brokers at scale. By offering purpose-built identification and entry administration, it extinguishes months of customized improvement whereas offering enterprise-grade safety. The service’s twin authentication mannequin, safe token vault, and seamless integration with present identification suppliers make it doable to deploy brokers that may safely function throughout organizational boundaries and entry numerous sources .As AI brokers develop into extra prevalent in enterprise environments, the necessity for sturdy identification and entry administration will solely develop. AgentCore Identification gives the muse for this future, enabling organizations to construct brokers that aren’t simply clever, but in addition safe, compliance-aligned, and reliable.
Sources to get began
Able to safe your AI brokers with AgentCore Identification? Listed below are your subsequent steps:
- Discover the documentation: Go to the Amazon Bedrock AgentCore documentation
- Strive the samples: Try the GitHub repository with full examples
- No value preview: You’ll be able to strive AgentCore providers at no further cost till September 16, 2025: Introducing Amazon Bedrock AgentCore: Securely deploy and function AI brokers at any scale (preview) | AWS Information Weblog
Begin constructing safe, scalable AI brokers in the present day with Amazon Bedrock AgentCore Identification. Rework your proof-of-concept into production-ready programs that meet the very best enterprise safety requirements.
Concerning the Authors
 Rahul Sharma is a Principal Product Supervisor-Technical at Amazon Net Providers with over 5 years of cumulative product administration expertise spanning Buyer Identification and Entry Administration (CIAM), Infrastructure as Code (IaC), and most not too long ago the agent identification area.
Rahul Sharma is a Principal Product Supervisor-Technical at Amazon Net Providers with over 5 years of cumulative product administration expertise spanning Buyer Identification and Entry Administration (CIAM), Infrastructure as Code (IaC), and most not too long ago the agent identification area.
 Fei Yuan is a Principal Engineer at AWS. Throughout his 20+ years of expertise, Fei has led completely different groups by way of varied tasks throughout Amazon and AWS, corresponding to Amazon Lending Market, Amazon Cost Providers, Alexa ML Safe Computing, Amazon DataZone, Amazon SageMaker information governance, and Amazon Cognito. Most not too long ago, he led the staff that launched Amazon Bedrock AgentCore Identification service. In the present day he focuses on designing and implementing AWS merchandise within the areas of agent identification, workload identification, and buyer identification and entry administration.
Fei Yuan is a Principal Engineer at AWS. Throughout his 20+ years of expertise, Fei has led completely different groups by way of varied tasks throughout Amazon and AWS, corresponding to Amazon Lending Market, Amazon Cost Providers, Alexa ML Safe Computing, Amazon DataZone, Amazon SageMaker information governance, and Amazon Cognito. Most not too long ago, he led the staff that launched Amazon Bedrock AgentCore Identification service. In the present day he focuses on designing and implementing AWS merchandise within the areas of agent identification, workload identification, and buyer identification and entry administration.
 Satveer Khurpa is a Sr. WW Specialist Options Architect, Amazon Bedrock at Amazon Net Providers, specializing in Amazon Bedrock safety. On this position, he makes use of his experience in cloud-based architectures to develop modern generative AI options for purchasers throughout numerous industries. Satveer makes use of his deep understanding of generative AI applied sciences and safety rules to design scalable, safe, and accountable purposes that unlock new enterprise alternatives and drive tangible worth whereas sustaining sturdy safety postures.
Satveer Khurpa is a Sr. WW Specialist Options Architect, Amazon Bedrock at Amazon Net Providers, specializing in Amazon Bedrock safety. On this position, he makes use of his experience in cloud-based architectures to develop modern generative AI options for purchasers throughout numerous industries. Satveer makes use of his deep understanding of generative AI applied sciences and safety rules to design scalable, safe, and accountable purposes that unlock new enterprise alternatives and drive tangible worth whereas sustaining sturdy safety postures.
 Antonio Rodriguez is a Principal Generative AI Specialist Options Architect at Amazon Net Providers. He helps firms of all sizes resolve their challenges, embrace innovation, and create new enterprise alternatives with Amazon Bedrock. Aside from work, he likes to spend time along with his household and play sports activities along with his mates.
Antonio Rodriguez is a Principal Generative AI Specialist Options Architect at Amazon Net Providers. He helps firms of all sizes resolve their challenges, embrace innovation, and create new enterprise alternatives with Amazon Bedrock. Aside from work, he likes to spend time along with his household and play sports activities along with his mates.