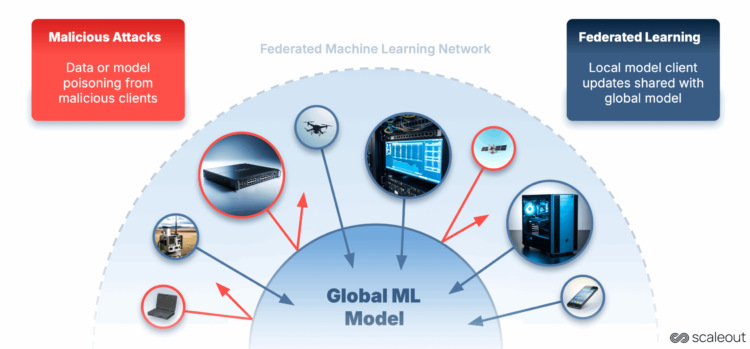
Federated Studying (FL) is we prepare AI fashions. As a substitute of sending all of your delicate knowledge to a central location, FL retains the information the place it’s, and solely shares mannequin updates. This preserves privateness and permits AI to run nearer to the place the information is generated.
Nevertheless, with computation and knowledge unfold throughout many units, new safety challenges come up. Attackers can be a part of the coaching course of and subtly affect it, resulting in degraded accuracy, biased outputs or hidden backdoors within the mannequin.
On this mission, we got down to examine how we will detect and mitigate such assaults in FL. To do that, we constructed a multi node simulator that allows researchers and trade professionals to breed assaults and take a look at defences extra effectively.
Why This Issues
- A non-technical Instance: Consider a shared recipe guide that cooks from many eating places contribute to. Every chef updates just a few recipes with their very own enhancements. A dishonest chef may intentionally add the unsuitable substances to sabotage the dish, or quietly insert a particular flavour that solely they know easy methods to repair. If nobody checks the recipes fastidiously, all future diners throughout all eating places may find yourself with ruined or manipulated meals.
- A Technical Instance: The identical idea seems in FL as knowledge poisoning (manipulating coaching examples) and mannequin poisoning (altering weight updates). These assaults are particularly damaging when the federation has non IID knowledge distributions, imbalanced knowledge partitions or late becoming a member of purchasers. Modern defences resembling Multi KRUM, Trimmed Imply and Divide and Conquer can nonetheless fail in sure eventualities.
Constructing the Multi Node FL Assault Simulator
To guage the resilience of federated studying towards real-world threats, we constructed a multi-node assault simulator on high of the Scaleout Methods FEDn framework. This simulator makes it potential to breed assaults, take a look at defences, and scale experiments with tons of and even 1000’s of purchasers in a managed setting.
Key capabilities:
- Versatile deployment: runs distributed FL jobs utilizing Kubernetes, Helm and Docker.
- Practical knowledge settings: Helps IID/non-IID label distributions, imbalanced knowledge partitions and late becoming a member of purchasers.
- Assault injection: Contains implementation of frequent poisoning assaults (Label Flipping, Little is Sufficient) and permits new assaults to be outlined with ease.
- Protection benchmarking: Integrates present aggregation methods (FedAvg, Trimmed Imply, Multi-KRUM, Divide and Conquer) and permits for experimentation and testing of a variety of defensive methods and aggregation guidelines.
- Scalable experimentation: Simulation parameters resembling variety of purchasers, malicious share and participation patterns may be tuned from one single configuration file.
Utilizing FEDn’s structure signifies that the simulations profit from the sturdy coaching orchestration, consumer administration and permits visible monitoring by means of the Studio net interface.
It is usually necessary to notice that the FEDn framework helps Server Capabilities. This characteristic makes it potential to implement new aggregation methods and consider them utilizing the assault simulator.
To start out with the primary instance mission utilizing FEDn, right here is the quickstart information.
The FEDn framework is free for all educational and analysis tasks, in addition to for industrial testing and trials.
The assault simulator is out there and able to use as an open supply software program.
The Assaults We Studied
- Label Flipping (Knowledge Poisoning) – Malicious purchasers flip labels of their native datasets, resembling altering “cat” to “canine” to scale back accuracy.
- Little is Sufficient (Mannequin Poisoning) – Attackers make small however focused changes to their mannequin updates to shift the worldwide mannequin output towards their very own objectives. On this thesis we utilized the Little is Sufficient assault each third spherical.
Past Assaults — Understanding Unintentional Influence
Whereas this research focuses on deliberate assaults, it’s equally priceless for understanding the consequences of marginal contributions brought on by misconfigurations or machine malfunctions in large-scale federations.
In our recipe instance, even an trustworthy chef would possibly unintentionally use the unsuitable ingredient as a result of their oven is damaged or their scale is inaccurate. The error is unintentional, however it nonetheless adjustments the shared recipe in ways in which may very well be dangerous if repeated by many contributors.
In cross-device or fleet studying setups, the place 1000’s or tens of millions of heterogeneous units contribute to a shared mannequin, defective sensors, outdated configurations or unstable connections can degrade mannequin efficiency in related methods to malicious assaults. Finding out assault resilience additionally reveals easy methods to make aggregation guidelines sturdy to such unintentional noise.
Mitigation Methods Defined
In FL, aggregation guidelines resolve easy methods to mix mannequin updates from purchasers. Strong aggregation guidelines intention to scale back the affect of outliers, whether or not brought on by malicious assaults or defective units. Listed below are the methods we examined:
- FedAvg (baseline) – Merely averages all updates with out filtering. Very susceptible to assaults.
- Trimmed Imply (TrMean) – Types every parameter throughout purchasers, then discards the best and lowest values earlier than averaging. Reduces excessive outliers however can miss refined assaults.
- Multi KRUM – Scores every replace by how shut it’s to its nearest neighbours in parameter area, maintaining solely these with the smallest complete distance. Very delicate to the variety of updates chosen (okay).
- EE Trimmed Imply (Newly developed) – An adaptive model of TrMean that makes use of epsilon–grasping scheduling to resolve when to check completely different consumer subsets. Extra resilient to altering consumer behaviour, late arrivals and non IID distributions.
tables and plots introduced on this publish had been initially designed by the Scaleout group.
Experiments
Throughout 180 experiments we evaluated completely different aggregation methods beneath various assault varieties, malicious consumer ratios and knowledge distributions. For additional particulars, please learn the full thesis right here .

The desk above reveals one of many sequence of experiments utilizing label-flipping assault with non-IID label distributed and partially imbalanced knowledge partitions. The desk reveals Check Accuracy and Check Loss AUC, computed over all collaborating purchasers. Every aggregation technique’s outcomes are proven in two rows, akin to the 2 late-policies (benign purchasers collaborating from the fifth spherical or malicious purchasers collaborating from the fifth spherical). Columns separate the outcomes on the three malicious proportions, yielding six experiment configurations per aggregation technique. The perfect end in every configuration is proven in daring.
Whereas the desk reveals a comparatively homogeneous response throughout all protection methods, the person plots current a totally completely different view. In FL, though a federation could attain a sure degree of accuracy, it’s equally necessary to look at consumer participation—particularly, which purchasers efficiently contributed to the coaching and which had been rejected as malicious. The next plots illustrate consumer participation beneath completely different protection methods.

With 20% malicious purchasers beneath a label-flipping assault on non-IID, partially imbalanced knowledge, Trimmed Imply (Fig-1) maintained total accuracy however by no means absolutely blocked any consumer from contributing. Whereas coordinate trimming decreased the impression of malicious updates, it filtered parameters individually somewhat than excluding complete purchasers, permitting each benign and malicious members to stay within the aggregation all through coaching.
In a situation with 30% late-joining malicious purchasers and non-IID , imbalanced knowledge, Multi-KRUM (Fig-2) mistakenly chosen a malicious replace from spherical 5 onward. Excessive knowledge heterogeneity made benign updates seem much less related, permitting the malicious replace to rank as probably the most central and persist in one-third of the aggregated mannequin for the remainder of coaching.

Why we’d like adaptive aggregation methods
Present sturdy aggregation guidelines, typically depend on static thresholds to resolve which consumer replace to incorporate in aggregating the brand new world mannequin. This highlights a shortcoming of present aggregation methods, which may make them susceptible to late collaborating purchasers, non-IID knowledge distributions or knowledge quantity imbalances between purchasers. These insights led us to develop EE-Trimmed Imply (EE-TrMean).
EE-TrMean: An epsilon grasping aggregation technique
EE-TrMean construct on the classical Trimmed Imply, however provides an exploration vs. exploitation, epsilon grasping layer for consumer choice.
- Exploration part: All purchasers are allowed to contribute and a standard Trimmed Imply aggregation spherical is executed.
- Exploitation part: The purchasers which have been trimmed the least can be included into the exploitation part, by means of a median rating system based mostly on earlier rounds it participated.
- The swap between the 2 phases is managed by the epsilon-greedy coverage with a decaying epsilon and an alpha ramp.
Every consumer earns a rating based mostly on whether or not its parameters survive trimming in every spherical. Over time the algorithm will more and more favor the best scoring purchasers, whereas sometimes exploring others to detect adjustments in behaviour. This adaptive method permits EE-TrMean to extend resilience in circumstances the place the information heterogeneity and malicious exercise is excessive.

In a label-flipping situation with 20% malicious purchasers and late benign joiners on non-IID, partially imbalanced knowledge, EE-TrMean (Fig-3) alternated between exploration and exploitation phases—initially permitting all purchasers, then selectively blocking low-scoring ones. Whereas it sometimes excluded a benign consumer because of knowledge heterogeneity (nonetheless significantly better than the identified methods), it efficiently recognized and minimized the contributions of malicious purchasers throughout coaching. This easy but highly effective modification improves the consumer’s contributions. The literature stories that so long as the vast majority of purchasers are trustworthy, the mannequin’s accuracy stays dependable.